

7 Wicked Trick or Treats to Protect Your Digital Footprint
Trick or Treat..
October is the month of spooky costumes and Halloween parties, but have you ever wondered what happens to your digital footprints while you are away from your device!?
Here are 7 wicked trick or treats you can easily act on to improve your cyber security posture and kick back and celebrate stress free.
# 1: “Think before you click”
Sounds obvious right?! But it can be easy to be fooled by a sophisticated phisher sending fraudulent emails to lure you to click-through and unwittingly expose yourself. They will do whatever they can to entice you into their bait. Whether it be winning a prize or any assortment of offers that are either too good to be true or almost believable (increasingly so).
To safeguard against this, it is best to learn how to outsmart phishing attacks, so you do not get hooked!
There are several ways to distinguish between a legitimate and a fake website link in an email.
Firstly, check the grammar and spelling of the email/message, see if there is anything suspicious about the sender’s number or email address.
Next, before you click on the enticing link, compare the legitimacy of the website address against a google search of the genuine company email. For example, if it’s a message or email from PayPal, the URL of the website should be PayPal.com, if the URL displays a domain that is different from the original (e.g., PayPa1.com), then most likely it will be a SCAM!
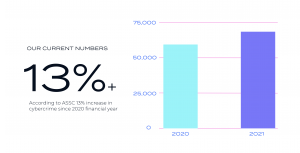
Reference: ACSC Annual Cyber Threat Report 2020-21 | Cyber.gov.au
#2: “What’s best to use for your password? A string on a cat’s whiskers”
If your password isn’t 15 characters long, you will be pawned!
As a best practice, it is now recommended you combine alpha numeric characters over a minimum of 15-characters in length. This increases the strength of your passwords exponentially and takes up to 2 centuries for a hacker to crack your password.
How are you supposed to remember 15+ characters? It’s straightforward. Forget passwords and think up passphrases instead. For example, #BestWitches4Halloween or @7hauntedhousesRspookY
Hot tips! It’s a great idea to use context-based passphrases for the ease of remembering your correct account password. And make sure to rotate your passwords every 3 – 4 months with automated password reminders.
#3: “Control + Alt + delete when you leave your seat”
Even working from home, get into the habit of locking your screen whenever when you need to take a quick bathroom break or grab another coffee. This cuts down the chances of spooky people controlling your device.
To lock your screen on a PC press Control + Alt + delete. And for laptops, press Windows + L (for Windows users) / Control-Command-Q (for Mac users).
When you leave your screen unlocked, you are more prone to getting hacked especially when you are nowhere in sight to monitor your devices. You are potentially leaving all the contents and data vulnerable to dark forces in the area to access your files.
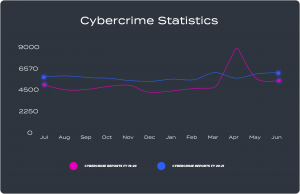
Reference: ACSC Annual Cyber Threat Report 2020-21 | Cyber.gov.au
#4. “An MFA a day, keeps the black hoodie guys away!!”
Multi-factor identification is a must! Although this will make it slightly longer to sign in, it is worth it. If you look closely behind the scenes, you will see a reduction of suspicious activity loitering in your devices.
Multi Factor Authentication is an additional layer of protection to signing in. It involves identity verification methods ranging from biometrics such as scanning a fingerprint or entering a one-time passcode from an authenticator app or text message.
By ensuring that MFA is imposed on all your business and personal accounts, this will help to prevent brute force attacks. And at the same time help you fulfil the security you need to comply with authentication standards in organisations.
#5: “Prepare for Disaster, recover faster”
Be it business or personal data if it’s not secure it is susceptible to attack. Adding encryption to even your backup devices which have very limited access is a prudent step, along with concurrently backing files and folders to help recover data in case of theft, loss or damages.
#6: “Don’t be shy about protecting PII”
Don’t hesitate to say “No!” when asked to disclose Personally Identifiable Information. PII is sensitive information about you including your name, date of birth, and credit card information – all of which should never be shared with a stranger. Insecure PIIs can lead to identity theft, fraud, and social engineering attacks.
#7: “We are one SOC away!”
Whoever you are, the threat of a cyber-attack is always on the horizon. With our digital world, every organisation is vulnerable and needs to be vigilant 24/7.
To sleep at night – you might consider investigating the total protection provided through a Security Operations Centre.
A SOC is a managed service with the sole focus of providing security protection. Provided in cloud and on a SaaS model – it is a cost-effective way for your organisation to achieve 24/7 visibility and a rapid response.
Armed with the latest technology, security teams can sense any unusual activity a mile away and near on instantaneously respond appropriately to the threat, well before any interruption to your services.
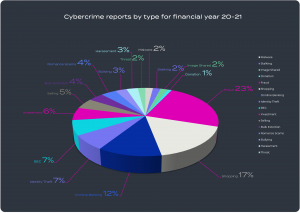
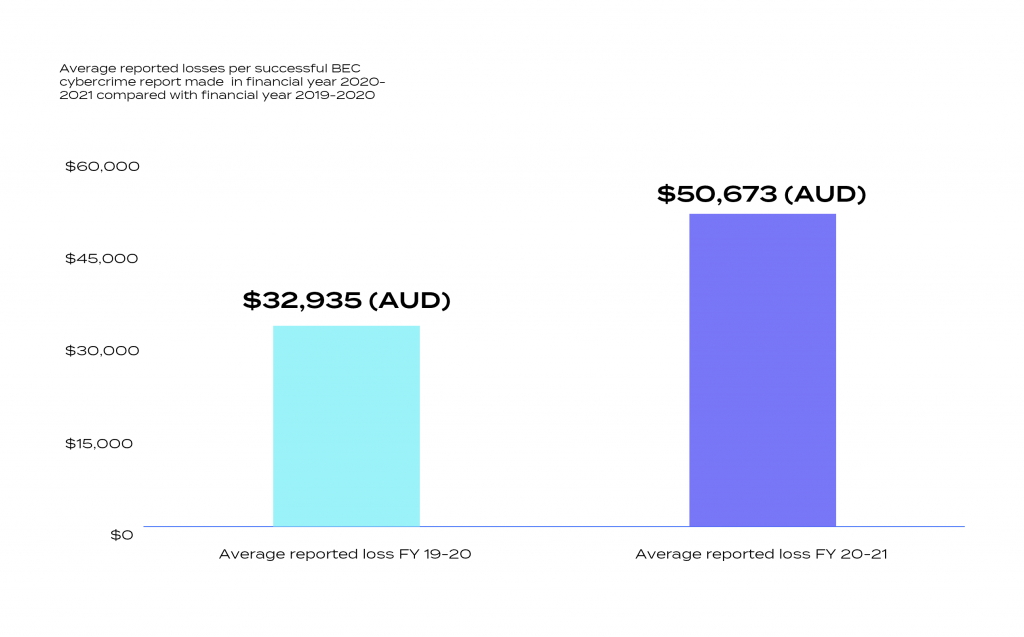
Reference: ACSC Annual Cyber Threat Report 2020-21 | Cyber.gov.au
Free! Take a trip in LAB3‘s Haunted House
To learn more about a SOC and your threat exposure, get in touch with the LAB3 security team. With a quick security scan (free!), they can quickly tell you what the internet already knows about you, and your organisation. You will be horrified!
Get in touch hello@lab3.com.au


 Linkedin
Linkedin
 Twitter
Twitter
 Facebook
Facebook
